Fully Homomorphic Encryption (FHE) is a revolutionary encryption technology that allows for securely processing encrypted data without prior decryption. This major advancement in the field of computer security opens new perspectives in privacy protection and securing sensitive data. In this thread, we will delve into the workings of FHE, its potential applications, and its implications for the future of data security. We will also compare it with other technologies such as Zero-Knowledge Proof (ZKP), and in the final part, we will share some FHE-utilizing projects that I’ve identified as interesting.

What is FHE: Fully Homomorphic Encryption
🔹 Encryption
Before understanding what FHE is, let’s first revisit basic encryption:
Encryption is a widely used method of securing data in cryptography. Its primary objective is to render data unreadable to anyone without the necessary key to decrypt it. This technique is essential for ensuring the confidentiality and security of sensitive information during transmission or storage.
The encryption process begins with converting plaintext data, also known as cleartext, into encrypted format using a specific algorithm and an encryption key. The result of this operation is the ciphertext. This ciphertext becomes unintelligible without the corresponding decryption key.
⚠️ It’s crucial to grasp and understand the concept of plaintext and ciphertext for the subsequent discussion (we’ll use it several times).
➮ There are two main types of encryption: symmetric encryption and asymmetric encryption.
Symmetric encryption uses the same key for both encryption and decryption. This means that the party encrypting the data and the one decrypting it must share the same secret key. While symmetric encryption is generally faster and less complex than asymmetric encryption, securely managing keys poses a major challenge.
Asymmetric encryption, also known as public-key encryption, uses two distinct keys: a public key and a private key. The public key is used to encrypt data, while the private key is used to decrypt it. This system allows anyone to encrypt data using the public key, but only authorized recipients possessing the corresponding private key can decrypt it. Does this story of private key/public key ring a bell?
Another thing: encryption can be either partially homomorphic or fully homomorphic. When only a limited number of operations can be performed on encrypted data, it’s called partially homomorphic encryption. On the other hand, if an unlimited number of operations can be performed on encrypted data, it’s referred to as fully homomorphic encryption (FHE).
🔹 A Bit of History First
In his doctoral thesis at Stanford University in 2009, American computer scientist Craig Gentry made a significant breakthrough by describing the very first fully homomorphic cryptosystem (or scheme). This groundbreaking achievement paved the way for a new era in cryptography, enabling complex operations on encrypted data without requiring decryption (we’ll get to that).
Gentry’s work thus marks the beginning of what’s known as Fully Homomorphic Encryption (FHE) cryptosystems. Since then, there has been evolution in this field. Since 2010, several generations of FHE cryptosystems (or schemes) have emerged. Each new generation represents an advancement over the previous one, offering improvements in terms of security, efficiency, and processing capabilities.
It’s important to note that each generation of FHE cryptosystems has specific characteristics that may be better suited to certain types of data or particular use cases. Therefore, the choice of FHE cryptosystem to use may depend on the context and requirements of the problem to be solved.
🔹 Basic Principles of FHE
Fully Homomorphic Encryption (FHE) is an encryption technique that allows for processing encrypted data as if it were plaintext, without ever needing to decrypt it. FHE relies on complex mathematical techniques, including linear algebra and number theory. Its operation is based on two fundamental operations: encryption and function evaluation.
Encryption is the process of converting data into unreadable text using an encryption key (as seen in the encryption section). Unlike traditional encryption where data must be decrypted to be processed, FHE allows for directly manipulating encrypted data without needing to decrypt it first.
Essentially, this means you can send encrypted data to a cloud service, for example, and ask it to perform calculations on this data without ever accessing its actual content. Once the calculations are done, the results are also encrypted, and you can decrypt them to obtain the final results. Don’t worry, we’ll explore more use cases in the next section.
Just before that, we recommend you take a look at this diagram, it explains the technical functioning of FHE quite well. The beginning of the diagram is at the top left: little 1 Data Owner.
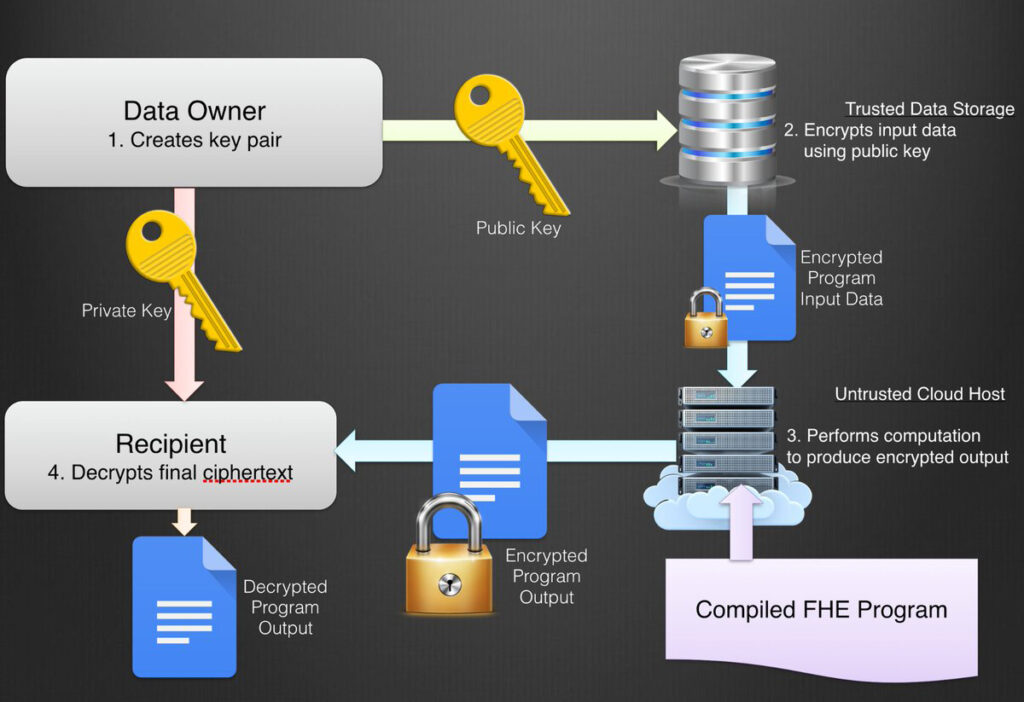
🔹 FHE Applications
FHE opens the door to numerous applications in various fields, including:
➮ Secure Cloud Computing Businesses can utilize FHE to process sensitive data in the cloud without compromising its confidentiality. For instance, complex calculations on medical data can be securely performed without revealing patients’ personal information.
➮ Privacy Protection Individual users can benefit from FHE to safeguard their online privacy. For example, messaging applications can employ FHE to encrypt end-to-end conversations, ensuring that even the service provider cannot access users’ messages.
➮ Secure Data Analytics Researchers and data analysts can leverage FHE to conduct analyses on sensitive datasets while preserving data confidentiality. For instance, studies on medical or financial data can be securely conducted without compromising the privacy of the individuals involved.
🔹 Crypto Use Cases
Fully Homomorphic Encryption could be particularly intriguing in the context of blockchain. Here are some reasons why FHE could be advantageous:
➮ Data Confidentiality: In blockchain, data is typically public and accessible to all participants. However, certain information may require confidentiality, such as personal or financial data. By using FHE, data can be stored in encrypted form on the blockchain while allowing authorized parties to perform calculations on this data without ever decrypting it, thus preserving its confidentiality.
➮ Secure Computations: FHE enables mathematical operations on encrypted data, paving the way for various applications in the blockchain domain. For example, smart contracts could perform calculations on encrypted data without compromising the confidentiality of the information involved.
➮ User Privacy Protection: By using FHE, blockchain users can benefit from privacy protection. For instance, financial applications on the blockchain could use FHE to conduct confidential transactions without revealing transaction details to unauthorized parties.
➮ Enhanced Security: FHE strengthens data security on the blockchain by minimizing risks associated with accidental or intentional disclosure of sensitive information. Even in the event of a compromise of a blockchain node, encrypted data remains inaccessible without the appropriate key.
🔹 Limitations and Challenges
While FHE offers significant advantages in terms of data security, it also presents limitations and challenges to consider, including:
➮ Computational Complexity: Operations on encrypted data can be much more complex and resource-intensive than operations on unencrypted data, leading to longer computation times and intensive use of computing resources. This can be particularly challenging in the case of blockchain, where we want transactions to be executed as quickly as possible.
➮ Key Size: The encryption keys used in FHE systems can be quite large, which may pose challenges in key management and performance.
The Different FHE Schemes
🔹 What is an FHE Scheme?
An “FHE scheme” refers to a set of specific rules and algorithms used to implement this encryption system. Imagine it as a detailed blueprint that defines how data is encrypted, decrypted, and how mathematical operations can be performed on encrypted data.
A scheme begins by defining the encryption process. This typically involves using a public key to transform data into an encrypted format, ensuring that only authorized individuals can access the plaintext data.
Next, the scheme also specifies how encrypted data can be decrypted using the corresponding private key. This step is crucial to ensure that data remains confidential and secure even when stored or processed in an untrusted environment.
An important aspect of an FHE scheme is its ability to perform homomorphic operations on encrypted data. The scheme defines which operations are allowed (e.g., addition, multiplication, etc.) and how they are carried out.
Security parameters are also defined in the FHE scheme. This includes elements such as key lengths, noise parameters, and other aspects related to the robustness of the cryptosystem against cryptographic attacks.
Finally, the scheme details the specific algorithms used to implement the various steps of the encryption, decryption, and homomorphic operations process. These algorithms ensure that FHE operates effectively and securely in practice.
🔹 The Different FHE Schemes
➮ GSW Scheme | Craig Gentry 2009
➮ DGHV Scheme | Marten van Dijk, Craig Gentry, Shai Halevi, and Vinod Vaikuntanathan 2010
➮ BGV Scheme | Brakerski-Gentry-Vaikuntanathan 2011
➮ BFV Scheme | Brakerski, Fan-Vercauteren 2012
➮ LTV Scheme | Lopez-Alt, Tromer, and Vaikuntanathan 2012
➮ BLLN Scheme | Bos, Lauter, Loftus, and Naehrig 2013
➮ CKKS Scheme | Cheon-Kim-Kim-Song 2016
There are likely others, but here are the main ones.
How does FHE differ from Zero-Knowledge Proof (ZKP)?
🔹 First, let’s revisit what Zero-Knowledge Proof is.
Zero-Knowledge Proof (ZKP) is a fundamental concept in cryptography that allows one party (the prover) to demonstrate to another party (the verifier) that they possess specific information without revealing that information itself. This means the prover can prove knowledge of information without disclosing the information itself.
ZKP is used in various domains, including computer system security, authentication protocols, and data privacy. It’s also widely used in cryptography.
🔹 Differences between ZKP and FHE
➮ Fundamental Objectives:
• FHE aims to enable computations on encrypted data without the need to decrypt it, thus preserving data confidentiality throughout operations.
• ZKP, on the other hand, seeks to prove the truth of a statement without revealing additional information other than the fact that the statement is true.
➮ Level of Confidentiality:
• FHE ensures total data confidentiality, even when subjected to operations. This means that even parties performing computations don’t have access to plaintext data.
• ZKP, however, doesn’t directly concern data confidentiality but rather the confidentiality of the proving process (it’s less confidential than FHE).
➮ Application Domains:
• FHE is particularly useful in areas such as cloud computing, where sensitive data must be processed confidentially even when handled by third parties.
• ZKP is widely used in applications such as identity-revealing authentication, electronic voting protocols, and blockchain systems where proving the validity of a transaction without revealing transaction details is crucial.
➮ Complexity and Performance:
• FHE is generally more complex in terms of implementation and performance. Operations on encrypted data can be much slower than operations on plaintext data, although significant progress has been made to improve FHE efficiency.
• ZKP may be less costly in terms of performance, but it depends on the specific protocol used and the nature of the statement being proved.
➮ Additional Info:
Zero-Knowledge Proofs (ZK) only allow for verifications, enabling encryption but cannot facilitate most encrypted computations due to the inability to combine private data from multiple parties.
In this sense, ZK is more relevant for scalability with a certain level of security, while FHE enables higher levels of data security associated with unprecedented use cases supported by its “holistic” encryption features, such as private on-chain auctions that are not achievable with ZK.
Some projects using FHE
As promised, I’ve selected 5 projects that we find really promising, using FHE, with or without tokens. These projects are very early and are worth keeping an eye on for 2024 – 2025.
🔹 Fhenix :
➮ Fhenix is the first confidential Layer 2 network powered by Fully Homomorphic Encryption (FHE).
➮ By utilizing fhEVM, Fhenix enables Ethereum developers to seamlessly build encrypted smart contracts and perform encrypted computations on data, all using Solidity and other familiar, easy-to-use tools. (We’ll discuss fhEVM further in the thread, so stay tuned.)
Whoa whoa whoa, what’s this FHE, “Fully Homomorphic Encryption” story about?
➮ Fully Homomorphic Encryption (FHE) is an advanced encryption technique that allows operations to be performed on encrypted data without needing to decrypt it first. Unlike traditional encryption, which requires decrypting data before processing, homomorphic encryption enables operations directly on encrypted data, thus preserving confidentiality.
➮ In other words, with FHE, it’s possible to perform calculations and operations on encrypted data, and the resulting output will also be encrypted. This provides a high level of privacy because sensitive data is never exposed in plaintext during processing.
➮ FHE has potentially significant applications in data privacy, computer security, and secure computing. In the context of Fhenix, FHE is used to enable computation on encrypted data while interacting with the Ethereum blockchain, thus providing an additional layer of privacy.
ℹ️ Information: For those unfamiliar with encryption principles, we ll briefly explain it here: Encryption is a security technique that transforms information into an unreadable format, called ciphertext. Encrypting something simply means making it difficult to understand without the appropriate decryption key. This helps protect the confidentiality of data when stored or transmitted over networks.
What makes Fhenix so special?
➮ FHE provides developers with superior technology to secure private data and perform encrypted computations, enabling a wide range of much-needed new use cases in Web3. Fhenix’s modular design makes seamless integration of FHE/encrypted computation across all layers of the blockchain easy and enables the effortless deployment of confidential smart contracts.
Is this similar to Zero-Knowledge Proof (ZKP) protocols?
➮ Not really. Is that answer okay? No, just kidding. Let me explain why and how.
➮ ZK proofs only allow for verifications, favoring scalability, but they don’t facilitate encrypted computation due to the inability to combine private data from multiple parties.
➮ In this sense, ZK is more relevant for scalability with a certain degree of security, while FHE enables higher levels of data security associated with unprecedented use cases supported by its “holistic” encryption features, such as private on-chain auctions.
Why is this important for Web3?
Data encryption is the final issue to solve in public blockchains, such as Ethereum. By using Fully Homomorphic Encryption (FHE) technology for confidential smart contracts, Fhenix can ensure exceptional levels of data security and pave the way for use cases in both blockchain and AI.
How does Fhenix enable encrypted computation?
By leveraging cutting-edge Fully Homomorphic Encryption technology, Fhenix enables privacy in smart contracts. Fully Homomorphic Encryption (FHE) facilitates computations on encrypted data without requiring decryption, as we’ve seen before. FHE has the potential to enable confidential smart contracts, ensuring that transaction inputs and states remain encrypted throughout the calculation process.
What is fhEVM?
fhEVM is a set of extensions for the Ethereum Virtual Machine (EVM) that allows developers to seamlessly integrate FHE into their workflows and create encrypted smart contracts without any cryptographic expertise, all while still coding in Solidity! The fhEVM protocol was initially developed by Zama, the leading cryptography company building open-source homomorphic encryption solutions for blockchain and AI, and has been directly integrated into the Fhenix network through a strategic partnership.
🔹 ZAMA:
ℹ️ Information: Before discussing Zama, we need to define what machine learning models are:
Machine learning models are like artificial brains (hence the name: artificial intelligence = AI). They allow computers to learn things by themselves from data, much like humans do. For example, imagine teaching a child to recognize animals. You show them images of animals and tell them what each one is. Over time, the child learns to distinguish a dog from a cat or a bird from a fish, even without your help.
Similarly, machine learning models learn from data. But instead of being taught by humans, they use algorithms to detect patterns in the data. For instance, a model could look at images of dogs and cats and learn to distinguish them by analyzing the visual characteristics of each animal.
Once a model has been trained with enough data, it can be used to make predictions on new data it has never seen before. For example, it can be used to automatically identify animals in new images. And the more images it sees, the more accurate it becomes in its predictions.
These models are used in various fields, such as speech recognition, online product recommendation, fraud detection in financial transactions, and much more. They open the door to all sorts of useful and innovative applications, enabling machines to learn and adapt autonomously.
➮ What is @zama_fhe?
ZAMA is a cryptography-focused company, specializing in developing privacy solutions for blockchain and artificial intelligence (AI). Its mission is to ensure data confidentiality in an ever-evolving digital world by providing innovative encryption tools and protocols.
➮ 1st Zama Solution: Concrete ML
Concrete ML, short for Concrete machine learning, is an open-source framework for machine learning focused on preserving privacy, based on fully homomorphic encryption (FHE). With Concrete ML, even if you’re not a cryptography expert, you can use artificial intelligence models while ensuring the privacy of your data (thanks to FHE). It allows you to train your models on encrypted data, thus ensuring a high level of confidentiality. This is done using familiar APIs from scikit-learn and PyTorch.
ℹ️ Information: For those wondering about Scikit-learn and PyTorch, read this: 👇
Scikit-learn: It’s a highly popular Python machine learning library that offers a wide range of algorithms and tools for data preprocessing, modeling, evaluation, and more. Its API is designed to be simple and intuitive, making it a preferred choice for machine learning beginners.
PyTorch: PyTorch is another Python library used primarily for deep learning. It offers flexibility and ease of use compared to other frameworks, and its dynamic API allows developers to build and deploy deep learning models effectively.
So when we talk about using “familiar APIs from scikit-learn and PyTorch” with Concrete ML, it means developers can use the same methods and functions they already know in these libraries to build and train machine learning models on encrypted data. This streamlines the development process and allows developers to leverage their existing experience using familiar tools.
With Concrete ML, you can use linear machine learning models, like logistic regression, trained using a technique called “federated learning.” In this approach, data privacy is protected using a trusted entity that securely aggregates information. This ensures data confidentiality without the need for encryption.
➮ 2nd Zama Solution: fhEVM
fhEVM, short for “Fully Homomorphic Encryption Virtual Machine,” is a technology developed by Zama that introduces smart contracts on a blockchain. Previously, there was a dilemma in the blockchain space: either keep your application and user data on-chain, making it visible to everyone, or keep it privately off-chain and lose contract composability. With FHE, Zama’s fhEVM makes it possible to execute confidential EVM smart contracts on encrypted data, ensuring both confidentiality and composability. 🔒
fhEVM contracts are built in the same way as smart contracts on Ethereum (or other EVM-compatible blockchains) using the Solidity programming language. Developers can use specific data types to mark parts of their contracts that need to remain private. Additionally, all access control logic for encrypted data is defined by developers in their smart contracts.
The use cases for fhEVM are numerous and varied. For example, it enables tokenization, blind auctions, on-chain games, and confidential voting, preventing the disclosure of sensitive data and protecting user privacy.
➮ What’s Zama’s Purpose?
ZAMA’s solutions address the needs of users and businesses across different sectors:
• Blockchain Privacy: ZAMA offers FHE encryption solutions for smart contracts with fhEVM, the first Fully Homomorphic Encryption-compatible EVM virtual machine. It enables confidential transaction execution and on-chain data protection.
• AI Privacy: Through Zama Concrete ML, ZAMA enables AI model training on encrypted data with FHE, thus ensuring the confidentiality of sensitive information. 🧠
• Personal Data Privacy: ZAMA provides solutions for secure collection, storage, and processing of personal data, in compliance with data privacy regulations such as GDPR.
➮ How Does It Work?
ZAMA provides 3 advanced cryptography techniques to ensure data confidentiality at every step of the process:
• Fully Homomorphic Encryption (FHE): No need to explain this one, we reckon.
• Secure Multi-Party Computation (MPC): By allowing multiple parties to collaborate on performing calculations on data without revealing sensitive information to each party, ZAMA ensures data confidentiality while enabling collaboration. More information will be provided on MPC in the upcoming thread on @Aleph__Zero!
• Zero-Knowledge Proof (ZKP): I’ve already explained this one well in part 3 so we won’t give you any more info.
Thanks to these technologies, ZAMA offers a comprehensive solution to ensure data confidentiality in a wide range of applications, paving the way for a new era of digital privacy.
🔹 Inco
Inco is a Layer 1 blockchain designed to enable the development of private dapps in Web3. It’s a modular confidential computing blockchain and a universal privacy Layer for Ethereum and other networks.
Inco leverages Ethereum’s security along with Fully Homomorphic Encryption (FHE) to create composable and usable confidential states. Inco’s main innovation lies in its use of fhEVM (FHE + EVM), which enables writing private smart contracts and performing computations on encrypted data without needing to decrypt them beforehand, all while being EVM-compatible!
➮ Why use Inco?
One of the main motivations for using Inco lies in its ability to store fully encrypted states on-chain. Unlike Zero Knowledge Proofs, which often require storing confidential data off-chain, Inco allows for a fully on-chain approach, making it composable, programmable, and trustless.
With Inco, developers can integrate privacy directly and simply onto the chain. They can use encryption/decryption, perform operations, and make comparisons on encrypted states within their applications, all using the Solidity programming language (used on Ethereum, for instance). This opens the door to a multitude of new use cases that were not possible with EVM and ZKP tools.
Finally, Inco also enables new use cases like an entirely new dApp design space. With fhEVM, it’s possible to explore new possibilities for dApp design and development, paving the way for new innovations in the blockchain and privacy domains.
➮ fhEVM
Before diving into explaining fhEVM in the context of @inconetwork, please read the 2 sections “ℹ️ Information” needed for understanding for the continuation👇
ℹ️ Information: What is precompilation?
When you write a computer program, whether it’s in a programming language like Python, Java, or Solidity, your computer can’t directly understand what you’ve written. It needs to be translated into a language that the computer can understand, which is typically machine language (binary), composed of 0s and 1s.
Compilation is the process of translating the source code, which you’ve written in a programming language, into machine code. Once your source code is compiled into machine code, it can be executed by the computer.
In the context of blockchain and smart contracts, compilation often occurs using specific tools provided by the blockchain platform, like the Solidity compiler for Ethereum. Once your smart contract is successfully compiled, it’s ready to be deployed on the blockchain and used by other users.
Now, precompilation is a process that occurs before the usual compilation. In this context, certain specific operations are precompiled, meaning they’re translated into machine language directly by the blockchain’s underlying software. This speeds up the execution of these operations because they don’t need to be recompiled every time they’re used in a smart contract.
ℹ️ Information: TFHE? Is it the same as FHE? No, not exactly:
TFHE (Torus Fully Homomorphic Encryption) is a specific variant of Fully Homomorphic Encryption (FHE). To understand TFHE, it’s helpful to briefly recall what FHE is.
Fully Homomorphic Encryption (FHE) is a cryptographic technique that allows mathematical operations to be performed on encrypted data without needing to decrypt it. This means that data can be encrypted and then securely manipulated without ever being exposed in an unencrypted form.
TFHE, on the other hand, is a specific implementation of FHE that focuses on optimization and efficiency. It uses mathematical structures based on the torus (a geometric shape) to perform encryption and decryption operations faster and more efficiently than traditional FHE methods.
One of the key features of TFHE is its use of bootstrapping, a technique that helps reduce the impact of noise growth, a common challenge in fully homomorphic encryption systems. By reducing this noise, TFHE can perform operations on encrypted data with better precision and performance.
So basically, TFHE is an optimized variant of FHE that uses special techniques to enhance the speed and efficiency of encryption and decryption operations on encrypted data.
fhEVM (Fully Homomorphic Encryption Virtual Machine) is an EVM-compatible virtual machine with TFHE (Torus Fully Homomorphic Encryption) added at the precompilation level. It enables homomorphic operations on both encrypted and unencrypted data. The homomorphic operations are exposed via a precompiled contract through static addresses, allowing developers to perform computations on data without needing to decrypt it beforehand.
The primary advantage of fhEVM is that it allows developers to use Ethereum and Solidity toolsets, including tools like Remix, Hardhat, and Metamask. Thus, developers can build their application logic in a familiar environment using the Solidity programming language. Seamless integration with existing toolsets is achieved through fhEVM precompiled contracts invoked via inline Yul assembly, while FHE functionalities are implemented as conventional Solidity functions or overloaded operators.
fhEVM also introduces:
- Encrypted integer data types (e.g., ebool, euint8, euint16, and euint32),
- TFHE operations ranging from arithmetic (e.g., TFHE.sub, TFHE.mul) to bitwise shifts (TFHE.shr, TFHE.xor, TFHE.and),
- And TFHE comparisons (e.g., TFHE.eq, TFHE.gt, TFHE.lt) that can be performed on encrypted values.
The gas price (transaction fees) for TFHE operations is configured at the contract level, providing greater flexibility compared to setting it at the bytecode level.
One more thing about fhEVM: the encryption and decryption processes are executed using a global network key distributed among validators. This distribution ensures that no individual entity can decrypt the blockchain state independently -> collective consensus must be achieved. The network key is generated during an initial setup phase orchestrated by founding validators, using a threshold protocol to enhance security.
➮ Ciphertext
When creating ciphertext on Inco, we take a plaintext message and transform it into an encrypted version using a special public key. At the same time, we generate a Zero-Knowledge Proof of Knowledge (ZKPoK) for the plaintext to ensure that the ciphertext is correct and that the user indeed knows the original value of the plaintext. This proof also ensures that the ciphertext cannot be misused elsewhere in the system.
When a user stores this ciphertext in a smart contract for the first time, the system verifies both the ciphertext and the associated ZKPoK proof. Then, the ciphertext is recorded on the blockchain, and a mapping is maintained between its location (handle) and its memory position. This allows tracking of all stored encrypted data and ensures that they remain secure and accessible only to authorized parties. Encrypted data types (euints) act as wrappers around this data, making it easier to identify and manage.
In summary, on Inco, ciphertext is considered valid only if its ZKPoK proof is also verified during the transaction, thus ensuring its security and integrity.
➮ Decryption and Re-encryption
To decrypt ciphertext, we have two options: use the TFHE.decrypt function or TFHE.reencrypt. When using TFHE.decrypt for regular decryption, the protocol validators execute a threshold protocol, meaning they must collectively agree to decrypt the ciphertext. The plaintext is then stored on the blockchain, where it can be publicly accessed by anyone.
On the other hand, TFHE.reencrypt allows for confidential decryption, where only the authorized user can access the plaintext. This process involves transforming the existing ciphertext into another ciphertext using a temporary public key provided by the user. Then, the user can decrypt the new ciphertext using a corresponding temporary private key. All of this occurs on the user’s side, ensuring data confidentiality and security.
🔹 Privasea
Privasea is the world’s first FHEML inference network. The network provides distributed computing resources for FHE AI operations. The entire system is supported by ZAMA’s machine learning seen previously (Concrete ML) and incentivized crowdfunding through $PRVA tokens (project tokens not yet released). In essence, Privasea is a network designed to address the challenges of AI computations and data privacy on the web. One small note: Privasea is backed by @BinanceLabs.
ℹ️ Information: Wait, what does inference mean? What’s this mess again?
Inference, in the context of AI and machine learning, refers to the process by which a computer system draws conclusions or predictions from provided data.
Think of it as how you might draw conclusions from the information you have. For example, if you see dark clouds in the sky, you might infer that it’s going to rain soon. In the field of AI, inference involves making decisions based on patterns or rules learned from previous data.
To simplify, inference involves using knowledge gained from data to make predictions or decisions about new, unseen data. It’s essentially the core of many AI systems that seek to understand, interpret, and act based on the information they receive.
ℹ️ Information: Okay, that’s cool, we’ve seen what inference is, but what about FHEML inference? 👇
“FHEML inference” refers to a process of inference in artificial intelligence (AI) that utilizes fully homomorphic encryption (FHE) technology. To fully grasp this concept, let’s break it down in a structured manner:
➮ Foundations of FHEML Inference: FHEML inference is based on the principle of FHE. Inference operations can be performed directly on encrypted data, thereby preserving their confidentiality throughout the process.
➮ Process of FHEML Inference: In FHEML inference, input data is initially encrypted using the FHE algorithm. Then, inference operations, such as classification or prediction, are performed on these encrypted data using machine learning models or other AI techniques. The results of the inference also remain encrypted throughout the process.
➮ Advantages of FHEML Inference: FHEML inference offers several pretty cool advantages. Firstly, it ensures data confidentiality by enabling inference operations on encrypted data, thereby reducing the risks of disclosing sensitive information. Additionally, it provides enhanced security by preventing unauthorized access to data during inference calculations.
➮ Applications of FHEML Inference: This approach finds applications in various domains where data privacy is important, such as healthcare, finance, and security. For example, in the healthcare domain, FHEML inference can be used to analyze sensitive medical data while preserving patient confidentiality.
➮ Challenges and Limitations: Despite its advantages, FHEML inference may also pose challenges, particularly in terms of performance and computational complexity. Operations on encrypted data can be more costly in terms of computation time and computational resources. Additionally, the effective implementation of this technique may require substantial technical expertise.
If we were to summarize what FHEML inference is, we would say that it’s an approach that enables performing AI inference operations on encrypted data, thereby preserving their confidentiality throughout the process.
Now that we’ve explained the important terms, let’s get back to Privasea.
Privasea provides a comprehensive solution to address the growing challenges of privacy and security in today’s digital world. Through a unique combination of cryptography expertise, cutting-edge technologies, and commitment to privacy, Privasea offers a range of services and solutions that redefine the standards for data security.
➮ Technologies used by Privasea
• Fully Homomorphic Encryption (FHE): Privasea utilizes FHE, which enables it to perform computational operations on encrypted data without decrypting it.
• Private Set Intersection (PSI): Privasea employs PSI to compare two sets of data without disclosing the specific details of each set. This allows for cross-analysis between different data sources without compromising privacy.
• Secure Biometric Algorithms: For human identity verification and other applications requiring biometric information, Privasea uses advanced algorithms to ensure the security and confidentiality of data.
➮ Solutions and Use Cases
Privasea offers a variety of solutions and use cases:
• Health Data Sharing: By encrypting electronic health records, Privasea enables individuals to securely share their health information with healthcare professionals without the risk of privacy breaches. 🩻
⚠️ The following point, in my opinion, is the most incredible solution offered by Privasea, so we will explain it in much more detail than the other points: 👇
• Facial Recognition Identity Verification: Using facial recognition and FHE, Privasea provides a secure solution for online identity verification, protecting users’ biometric data. Privasea can thus be a solution against Sybil attacks.
ℹ️ Information: What is a Sybil attack?
A Sybil attack is a form of cyber attack where an individual or group creates multiple virtual identities (called “sybils”) to manipulate a system or online community. These identities appear to be different users but are all controlled by the same malicious entity.
The main objective of a Sybil attack is often to deceive or manipulate other users or the system itself. For example, on social networks, a Sybil attacker could create multiple accounts to artificially increase the number of followers or interactions on a post, giving the impression that an idea or product is more popular than it actually is. So, as you might understand, a Sybil attack is not great for all types of networks, especially a blockchain network.
But how does it work in practice?
Privasea provides a human likeness attestation application using Fully Homomorphic Encryption (FHE) technology, offering a secure and private solution for human identity recognition. In a world where bots and fake profiles abound, Privasea ensures user authenticity by providing a human likeness attestation without the need to manage or store biometric data. This application utilizes an encrypted computation process, making it impossible for even the application operators to access users’ biometric data: the FHE.
Security is a priority with Privasea, which ensures a genuine attestation of human likeness. Users can display their Privasea badge on their social and online Web3 profiles, thereby demonstrating their authenticity and commitment to true human identity.
Privacy is also a crucial aspect of Privasea. Through FHE cryptography, all data is encrypted, meaning that even the application developers cannot access users’ biometric information. Thus, no biometric or personally identifiable data is stored in an unencrypted state, ensuring true user privacy protection.
In terms of ease of use, Privasea simplifies the process of verifying human identity. Users can simply open the application on their phone and scan their face to obtain the Privasea human likeness attestation badge, without the need to travel to a city. Once verified, an NFT is awarded to their wallet as attestation badges.
“without the need to travel to a city” refers to Worldcoin ( @worldcoin $WLD), which is a project that attests that the owner of a Worldcoin wallet is indeed human by scanning the pupil, a process that requires individuals to travel to cities where Worldcoin devices (Orbs) are deployed to scan their eyes. This approach is therefore impractical compared to the solution proposed by Privasea.
Thus, this human recognition offered by Privasea will allow, for example, certification of human eligibility for a crypto airdrop, for instance. It will mainly address the issue of Sybil attacks as a whole, and that’s quite powerful.
• Analysis of Data on Encrypted Sets: Privasea enables the analysis of large datasets while preserving confidentiality through the use of FHE. This allows businesses and researchers to extract useful information without compromising data privacy.
➮ Commitment to Privacy and Security
Lastly, Privasea stands out for its commitment to the privacy and security of its users’ data. By integrating advanced technologies, robust security protocols, and data protection practices, Privasea assures its users that their information is in good hands.


